Security Status
Access Control

Allow company entry through facial recognition/fingerprint registration
Restrict visitor access/Log visitor details upon entry
Internal & External Security Equipment

Real-time surveillance with external building CCTV
Prevent intrusion with external infrared sensors
Night security managed by professional security company (S1)
Internal Network/Internet Network Separation (Network Integration)

Block external intrusion with network separation between internet and security work areas
Establish an internal network integration (data transfer) system
Encrypt all data through DRM
Monitor external leakage of critical data through DLP
Manage and control digital asset usage rights through DRM
IT Security
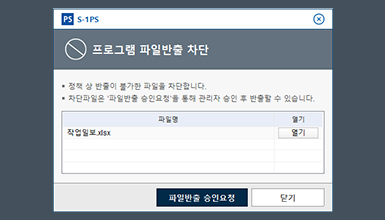
Detect and control network access through NAC
Block usage of portable storage devices
Restrict file attachments via the internet
Prevent software file extraction
Manage website access and software execution
Facility security
- Access Control
- Allow company entry through facial recognition/fingerprint registration Restrict visitor access/Log visitor details upon entry

- Internal & External Security Equipment
- Real-time surveillance with external building CCTV Prevent intrusion with external infrared sensors Night security managed by professional security company (S1)

information security
- Internal Network/Internet Network Separation (Network Integration)
- Block external intrusion with network separation between internet and security work areas Establish an internal network integration (data transfer) system Encrypt all data through DRM Monitor external leakage of critical data through DLP Manage and control digital asset usage rights through DRM

- IT Security
- Detect and control network access through NAC Block usage of portable storage devices Restrict file attachments via the internet Prevent software file extraction Manage website access and software execution



